Sql Injection & Hash Decrypting (Advanced)
Step 0: Collecting Information
Directory structure
First of all we try to get as much information as we can, starting with the navigation:
| C:\Program Files\Apache Group\Apache2\ENRP\
|__ index.php |__ news.php |__ action=news.php |__ method=GET |__ param=month [all, September, …] |__ debates.php |__ members.php |__ newsletter.php |__ mailinglist.php |__ action=addmail.php |__ method=POST |__ field=email |__ speeches.php |__ action=speeches2.php |__ method=POST |__ field=speech [1] |__ press.php |__ action=readpress.php |__ method=POST |__ field=release [1, 2, 3] |__ economy.php |__ speeches/ |__ passwords/ |
We know the root path from an error that we get by calling readpress.php page without parameter. In addition, this error tells us that there is also a second directory structure as follows:
| C:\Program Files\Apache Group\Apache2\htdocs\ENRP\includes\
|__ special.php |__ �ooter.php |__ arrange.php |
Database model
From the same error and also by calling news.php file witout parameter, we learn these information from the database model:
|
|
||||||||||||||||
Errors
news.php without parameter produces following error:
| MySQL Error Reported: row “january” does not exist
Error in query: “SELECT post, date FROM newsTable WHERE month =”January” |
readpress.php without parameter produces following error:
| MySQL Error: “” row does not exist in table “press_table”;
Warning: Unexpected character in input: ‘\’ (ASCII=92) state=1 in C:\Program Files\Apache Group\Apache2\ENRP\readpress.php on line 33 Error in query: error_reporting(E_ALL); $service_port = “80”; $address = “localhost”; $socket = socket_create(AF_INET, SOCK_STREAM, SOL_TCP); $in = “GET /speeches/passwords/” . md5(‘Speeches’) . “”; $in .= “REFERER: http://ENRP/get_speeches_passwords_referer\n”; $in .= “\n\n”; $out = ; socket_write($socket, $in, strlen($in)); echo “OK.\n”; include(\”C:\Program Files\Apache Group\Apache2\htdocs\ENRP\includes\special.php\”); include(\”C:\Program Files\Apache Group\Apache2\htdocs\ENRP\includes�ooter.php\”); include(\”C:\Program Files\Apache Group\Apache2\htdocs\ENRP\includes\arrange.php\”); ?> |
Step 1: Find an access
Find account
The second error gives us a directory structure:
| GET /speeches/passwords/” . md5(‘Speeches’) |
As we can see, there is a sub directory inside /speeches/passwords/, encrypted with MD5. Using e.g. Python, we get the MD5 hash of the string “Speeches”:
| $ python
>>> import hashlib >>> hashlib.md5(‘Speeches’).hexdigest() ‘7e40c181f9221f9c613adf8bb8136ea8’ |
Full URL becomes:
We can see that the directory contains a file named passwords.fip. By clicking on it, we get two passwords, separated by colon.
| 7bc35830abab8fced52657d38ea048df:21232f297a57a5a743894a0e4a801fc3 |
Crack MD5 hashes
Following site has a huge database of MD5 hashes:
http://www.tmto.org/?category=main&page=search_md5
It helps us finding this username:password = moni1:admin .There are many softwares and online sites for cracking it.
Step 3: Log-in
The fake authentication form
The site is likely to have an administration access. It is often named “admin”, “adm”, “conf”, … Let’s try “admin”:
http://www.hackthissite.org/missions/realistic/13/admin/
By using our discovered credentials, we get an error:
“admin” does not match password for “moni1”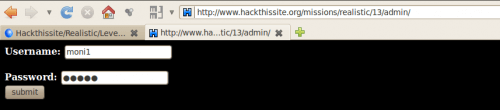
The right authentication form
Let’s replace “admin” with its MD5 hash (21232f297a57a5a743894a0e4a801fc3)
http://www.hackthissite.org/missions/realistic/13/21232f297a57a5a743894a0e4a801fc3/
|
And this time it should work. Access granted, mission completed!


