Perl Script Injection
Collecting Information
Global structure
The first thing we have to do is to get as much information as we can about this portal. We immediately notice that the portal is based on a frameset with:
|
Read files
In addition, by clicking on student work > Joey Simons > Sign my guestbook, we see a form. Here is the source code
| <html><head><title></title></head>
<body bgcolor=”#ffffff” text=”#000000″> <form action=”../cgi-bin/guest.pl”> <input type=”hidden” name=”action” value=”write”> |
Message:
| <input type=”text” name=”text” size=50>
<input type=”submit” value=”submit”> </form> </body></html> |
We notice that:
|
Access hard drive
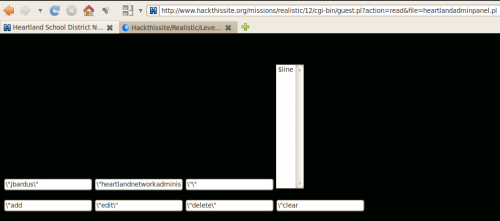
The main controller (internet.pl) is not protected. Indeed, it is possible to request the hard drive content by injecting “file://” instead of “http://”. We discover a new form, named “heartlandadminpanel.html” in C:\WEB\HTML: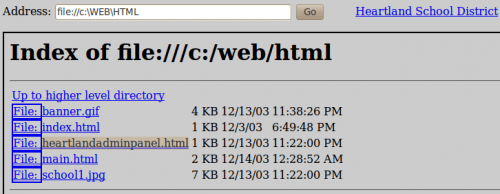
Here is what it looks like (http://www.hackthissite.org/missions/realistic/12/heartlandadminpanel.html)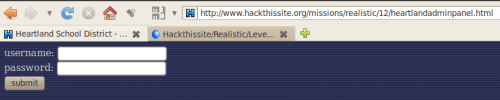
By viewing the source code of this page, we notice that the form action is
| cgi-bin/heartlandadminpanel.pl |
Our first mission is to find valid credential to access the protected content.
Step 1: Find valid credential
Using our *fake* file editor, we are going to view the content of cgi-bin/heartlandadminpanel.pl file. To do so, we are going to enter this address in our URL bar:
|
Here is what it produces:
The source code of the page gives us the information we are looking for: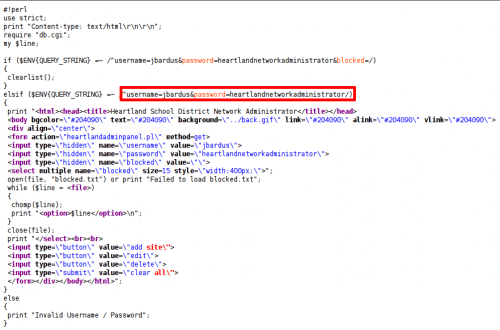
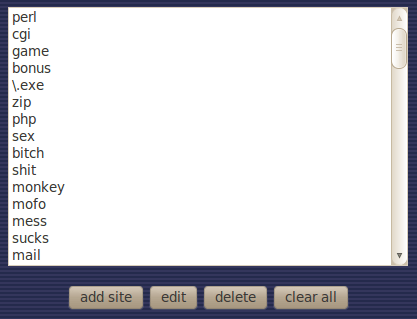
Step 2: Delete list
Access this page:
http://www.hackthissite.org/missions/realistic/12/heartlandadminpanel.html
And log in with:
|
Click on “clear all” button and you’re done!