User-Agent Spoofing & Cookie Injection
There are a lot of things going on with this mission and if you have been following my other tutorials you should be all set understanding how to accomplish this mission.
It seems Zach is having an issue with his grades at school and has asked us to help him change them.
The very first thing we do (and I have been saying this since basic 1) is explore each page and view the source of each page.When I did this I notice that the home page had a blank image link to a page called staff.php
| <a href=”staff.php”><img src=”nothing.gif” width=150 height=20 border=0></a> |
This page brings us to a login page. Now I spent some time trying to find a hole and was unsuccessful. I talked to a friend of mine and he said he guessed the username and password.
| username: smiller password: smiller |
It is just so called famous brute-force method. Most common weak admin/password list:
admin:admin
admin:password
username:password
username:terminal
admin:sitename
username:sitename
admin:email
username:email
Now that we are able to login you notice the following:
| Welcome, Mrs. Samantha Miller! Please remember that access to the staff administration area is restricted to the district-supplied ‘holy_teacher’ web browser. |
It appears that the page is checking the User-Agent. A user agent is the client application used with a particular network protocol; the phrase is most commonly used in reference to those which access the World Wide Web, but other systems such as SIP use the term user agent to refer to the user’s phone. Web user agents range from web browsers and e-mail clients to search engine crawlers (“spiders”), as well as mobile phones, screen readers and braille browsers used by people with disabilities. When Internet users visit a web site, a text string is generally sent to identify the user agent to the server. This forms part of the HTTP request, prefixed with User-Agent: (case does not matter) and typically includes information such as the application name, version, host operating system, and language. Bots, such as web crawlers, often also include a URL and/or e-mail address so that the webmaster can contact the operator of the bot.
You can use any add-on to change the user-agent. Here the usage of “Tamper Data” and “User Agent Switcher” is shown
====Tamper Data====
To get around this we can use FireFox and an add-on called TamperData. If you have been following along my other examples you should already have this software installed. Open Tamper Data :
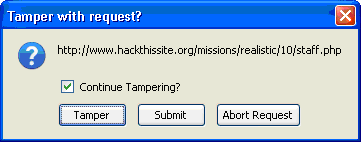
And Click start Tamper. Now enter in the username and password. you should get the following dialog box:
You want to click on the Tamper button and you should get the following screen:
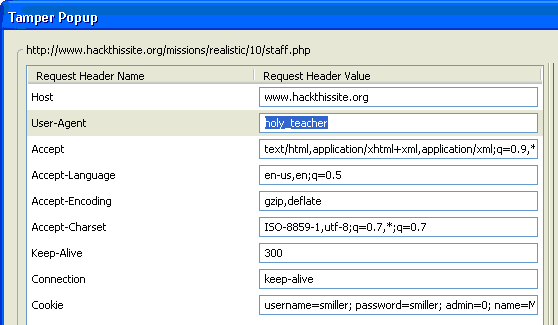
You will notice a User-Agent field. You will have to change this field to : “holy_teacher”
Keep in mind every time you send a request you will have to change the User-Agent.
Keep in mind every time you send a request you will have to change the User-Agent.
Now you are able to log in…Great!
====USER AGENT SWITCHER====
To be able to connect, we have to modify the user-agent of our
browser. We can achieve this by using “User Agent Switcher” for Firefox.
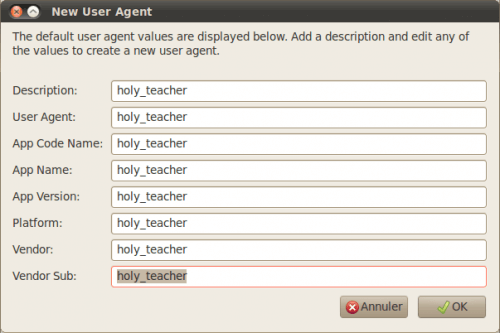
Create a new profile and fill in all fields as follows:
Change your user-agent by loading your new profile and refresh page. You are now able to access the administration module:
========